Software Security for Mobile Devices
Scenario and Motivation
In 2015, Android accounts for about 80% of all shipments of smartphones worldwide. Hence, Android has become a prime target for attackers to, e.g., steal private user data. Despite existing security mechanisms like sandboxes for isolation of apps and permissions to control access to critical resources, reports about security violations by Android applications, such as GPS coordinates leaking out of the device , appear frequently.
Apps should be secure and, ideally, developers should provide the desired security guarantees for their apps. However, it is not always possible that the developer provides all desired security guarantees. For instance, if the developer was not aware of the security requirements of a user, or if different users have different security requirements.
We want to enable end-users to ensure that all apps they are using satisfy their individual security requirements.
Approach
We enable end-users to ensure that all apps that they use respect their individual security requirements by integrating security technologies into a certifying app store. For different kinds of security requirements, different security technologies can be integrated. Besides common functionality of an app store for installing apps, our app store can:
- visualize security guarantees the developer of an app provides (see picture on the left below)
- check before installation whether an app keeps data the user considers confidential secret (see picture in the middle below)
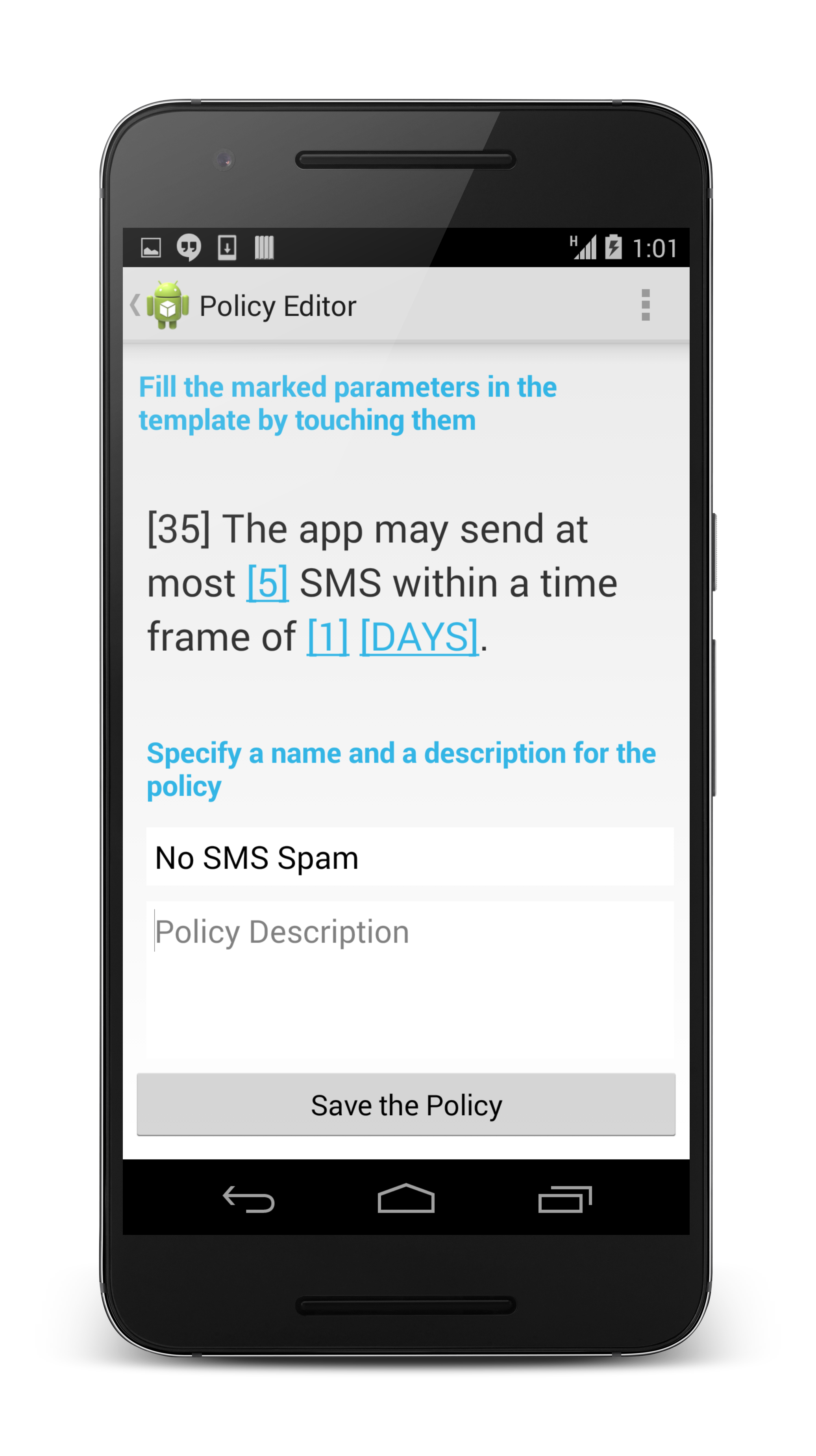
- prevent undesired behavior like SMS spamming while an app is running (see picture on the right below)
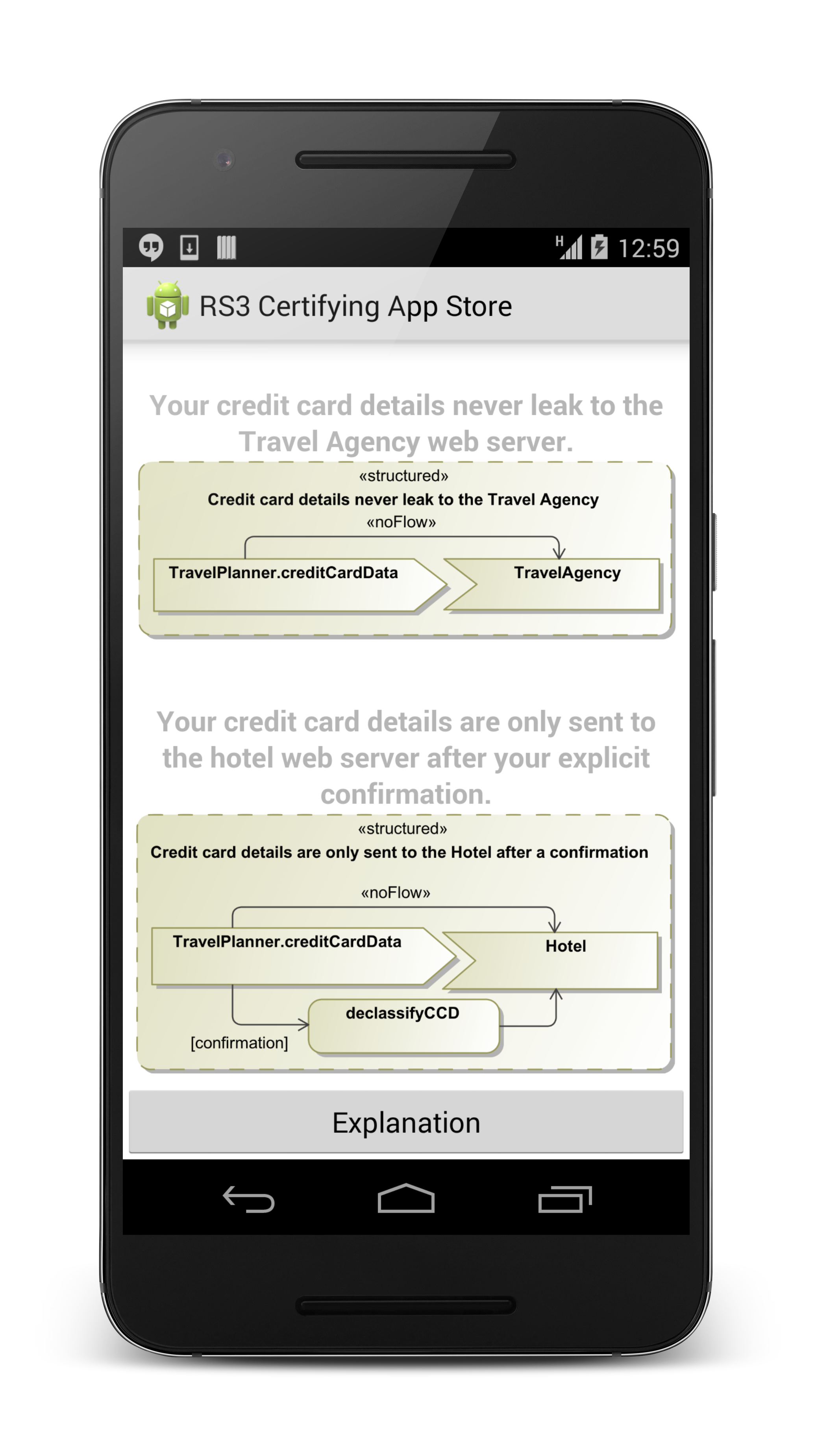
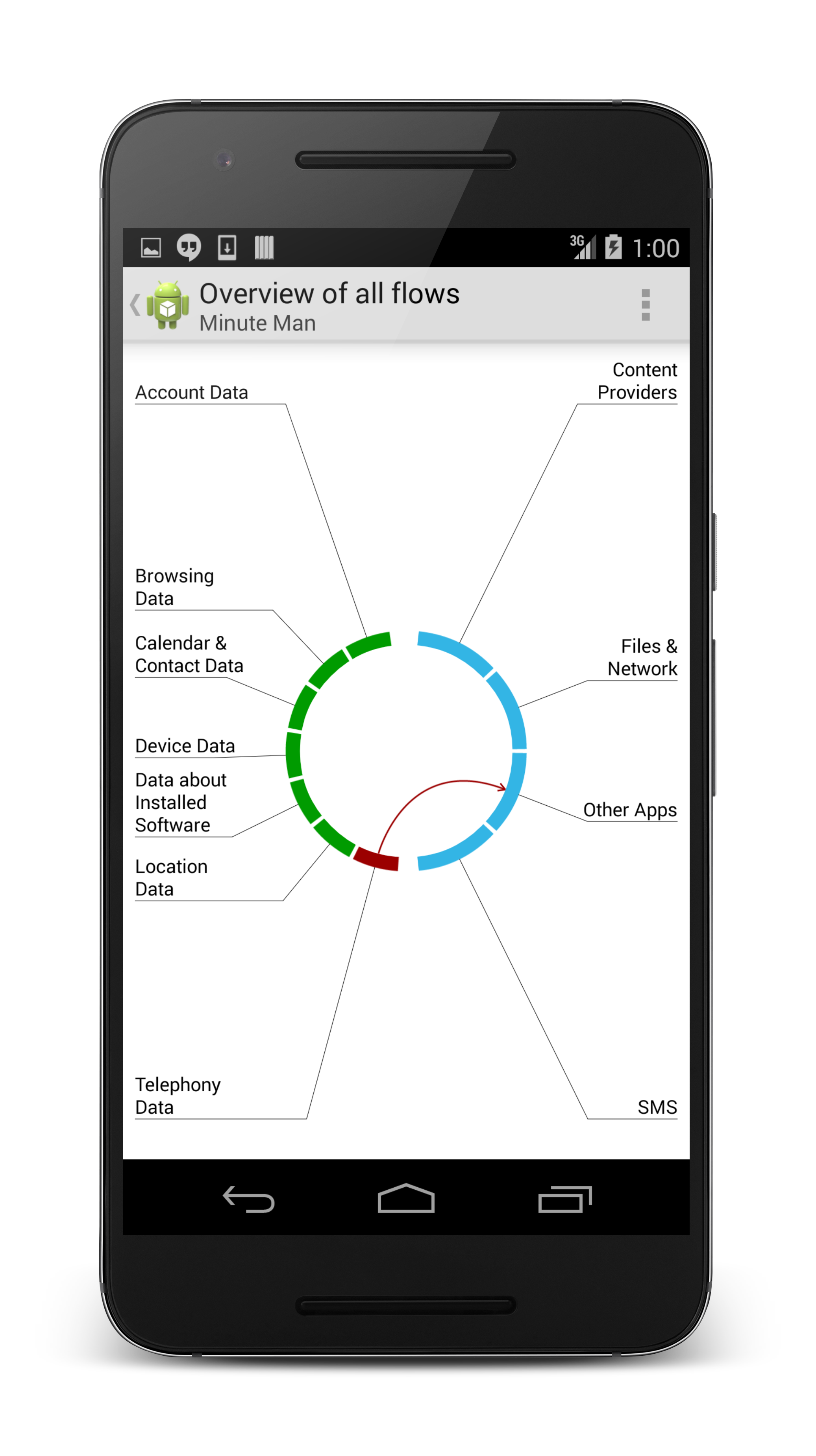
Overall, the certifying app store is a one-stop solution for browsing and installing apps as well as ensuring that the apps adhere to the security requirements desired by the end-user. The integration of the techniques for ensuring security of the apps into the certifying app store puts these techniques to the default entry point for new apps to a smart-phone.
Solution and Product
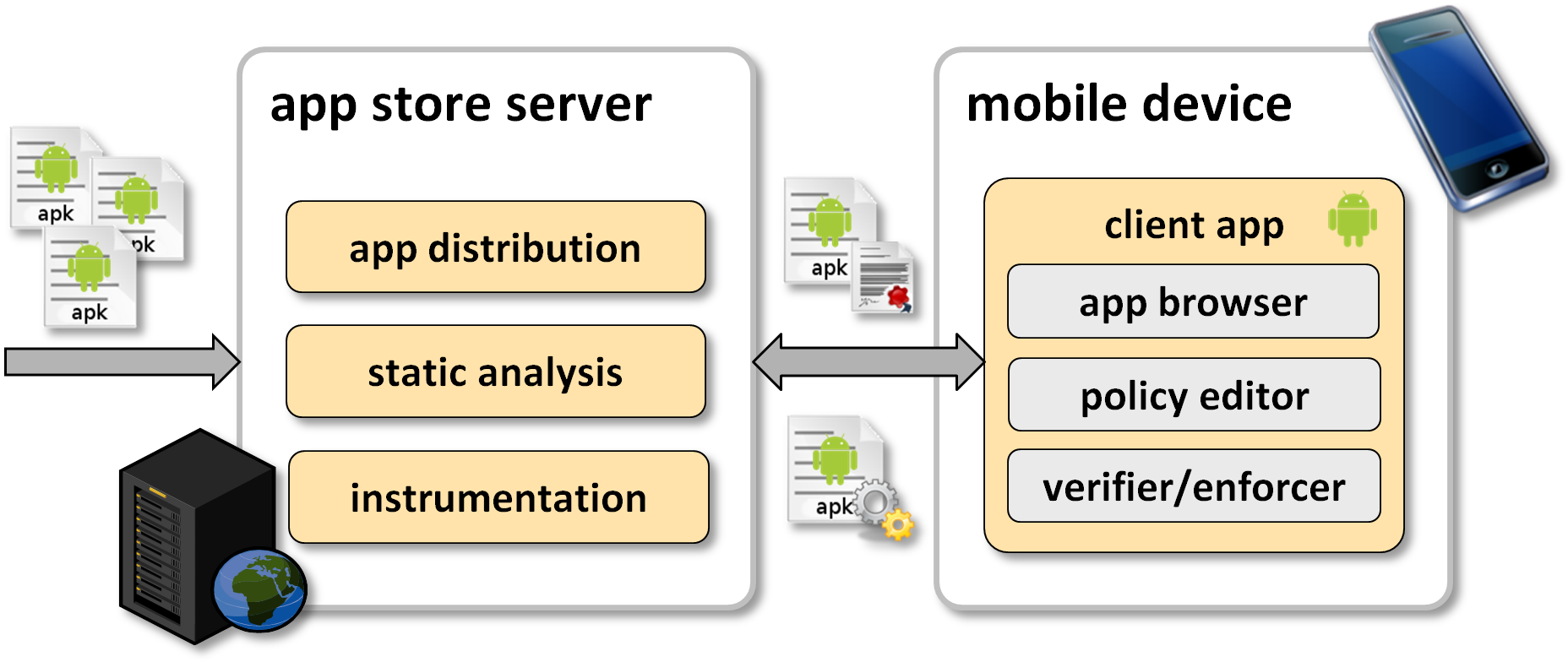
The RS3 Certifying App Store realizes our approach. It implements a client-server architecture (see the picture below).
The server of the RS3 Certifying App Store comprises a database of apps together with the guarantees provided by their developers, the static analysis modules for checking whether an app keeps the information a user considers confidential secret and the instrumentation module for the runtime monitoring to prevent undesired behavior.
The client of the RS3 Certifying App Store is an Android app that can run on off-the-shelf smart phones. It provides an interface for end-users to browse apps, check the security requirements a developer provides, specify their desired security requirements, triggering the security tools on these apps and install the apps to their phone.
The static analysis modules implement information-flow analyses. Two different modules can be chosen by the end-user:
- a type system that leverages the benefits of proof-carrying code to remove the server of the RS3 Certifying App Store from the trusted computing base
- a PDG-based slicing that leverages the power of object-sensitive and context-sensitive program analyses for precise analysis results
The instrumentation module implements a code transformation. It inserts code into an app that sends security critical events to the policy decision point integrated into the client of the RS3 Certifying App Store when the program runs. The policy decision point then decides based on the user-specified policy whether the action associated with the event shall be permitted.
Impact and Highlights
User-defined Policies:
The RS3 Certifying App Store supports user-defined policies to express the personal security requirements of an end-user. For the information-flow analysis, the user can select from a list of information sources which information he considers confidential and which information sinks he considers public. For the runtime enforcement the user can instantiate policy templates with concrete values to specify the behavior he wants to enforce.
User-friendly Presentation of Security Guarantees:
The results of the static analyses as well as the policies enforced by the runtime monitoring abstract from technical details to make them more amenable to non-expert users. The graphical presentation of the analysis results provides an overview on the information flows in an app. The textual representation of the runtime policies additionally serves as an intuitive description of the policy.
Integration of State-of-the-Art Security Technologies for Different Guarantees:
The RS3 Certifying App Store is a one-stop solution for end-users to install apps that adhere to their personal security requirements. To this end, it integrates information-flow type systems with proof-carrying code implemented in the RSCP analyzer, PDG-based information-flow analyses building on state-of-the-art program analyses implemented in JoDroid, and usage control based on runtime monitoring implemented in DroidForce.
Selected Publications
| [1] | Cassandra: Towards a Certifying App Store for Android. S. Lortz, H. Mantel, A. Starostin, T. Bähr, D. Schneider, and A. Weber. In 4th ACM CCS Workshop on Security and Privacy in Smartphones and Mobile Devices, 2014. |
| [2] | DROIDFORCE: Enforcing Complex, Data-Centric, System-Wide Policies in Android. S. Rasthofer, S. Arzt, E. Lovat, E. Bodden. In 9th International IEEE Conference on Availability, Reliability and Security, 2014. |
| [3] | JoDroid: Adding Android Support to a Static Information Flow Control Tool. M. Mohr, J. Graf, M. Hecker. In Software Engineering (Workshops), 2015. |
| [4] | Software security for mobile devices. S. Arzt, A. Bartel, R. Gay, S. Lortz, E. Lovat, H. Mantel, M. Mohr, B. Nordhoff, M. Perner, S. Rasthofer, D. Schneider, G. Snelting, A. Starostin, A. Weber. Poster at the 36th IEEE Symposium on Security and Privacy. |